OT security model, Risk assessment, and Management
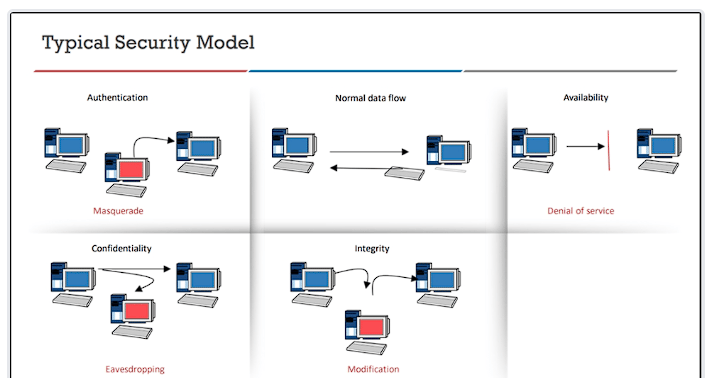
Typical Security Model
As you look at this model, it is important to understand that the top example is our normal data flow and when you look at it and break it down into components you can see that there are multiple areas that when you approach it from the view of an attacker can be used to gain an advantage
Typical Security Model
The first step we look at is the authentication, can we present credentials and get access to a system, then we have the same concepts from the attacker side and that is can we present credentials that allow us to masquerade or spoof an authorized users identity and in effect “masquerade” as a legitimate user.
The next part of the model we will review is the desire to protect the confidentiality of our systems, we want to ensure that the data we communicate is protected; furthermore, it is not intercepted by an adversary and that is how when we put on our “hacker” hat we intercept or eavesdrop on the communication between a client and a server and thus the confidentiality is compromised.
What if as a user we want to ensure our data is valid and correct? We need to ensure the data integrity of the information that traverses the network. From the “attacker” view we want to change this data, or better put we want to modify it and that is the attack against the integrity of data. As an example, if a user is making a transaction, we can modify the amount of the account number, either of this compromises the integrity of the data.
The last component of our example model here and one of the most difficult to secure is maintaining the availability of our systems and or networks. This availability becomes a challenge because an attacker just wants to degrade or interrupt this service. Since as a service we have to provide the ability to access it, we can then leverage that requirement and attack it! We know the service has to be available; therefore, we have a 100% guarantee that the service will be accessible, and all finite resources can be flooded, so all we have to do is send enough data to flood or degrade the services which is the only goal of the attack. While all of this is a concern, we can take comfort in the fact that hackers need services, so for the most part they do not want to perform a Denial of Service. There is also another reason and that is if all we can do is flood services then that is an admission of failure.
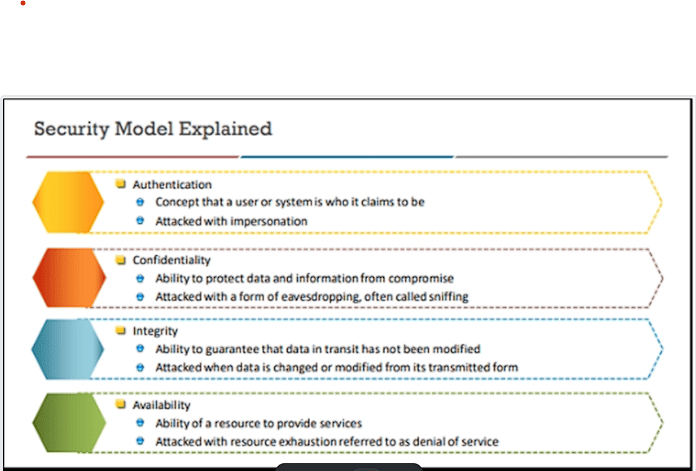
Security Model Explained
This is an expansion on the security model. As you review the components here you see that there is something missing? This model is one of many different models that are availability in the industry, and it does take into account Authentication which the traditional CIA Triad model does not.
The CIA (Confidentiality, Integrity, and Availability) triad of information security is an information security benchmark model used to evaluate the information security of an organization.
The CIA triad of information security implements security using three key areas related to information systems including confidentiality, integrity, and availability.
Security Model
The CIA triad of information security was created to provide a baseline standard for evaluating and implementing information security regardless of the underlying system and/or organization.
The three core goals have distinct requirements and processes within each other.
Confidentiality: Ensures that data or an information system is accessed by only an authorized person. User Id’s and passwords, access control lists (ACL) and policy-based security are some of the methods through which confidentiality is achieved.
Integrity: Integrity assures that the data or information system can be trusted. Ensures that it is edited by only authorized persons and remains in its original state when at rest. Data encryption and hashing algorithms are key processes in providing integrity.
Availability: Data and information systems are available when required. Hardware maintenance, software patching/upgrading, and network optimization ensures availability.
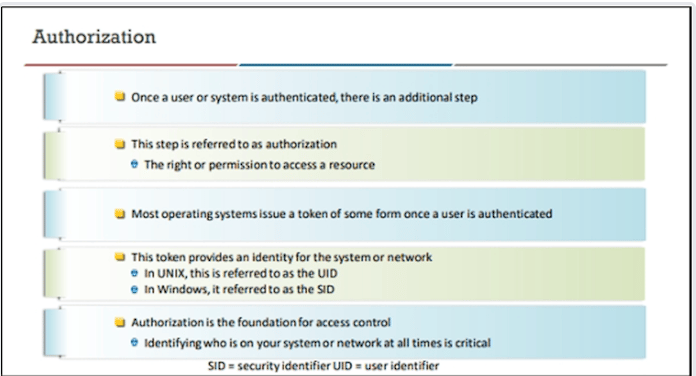
Authorization
As we have reviewed these different models, none of them have addressed a very important component that defines what happens once we get into the system? This is the sole reason for having different types of access control systems, we have the
DAC – Discretionary Access Control
Which gives us the concept of a different users based on privileges.
MAC – Mandatory Access Control
Where a higher level of protection is available that means even a system owner cannot change permissions, examples of this are AppArmor and SELinux
RBAC - Role Based Access Control
Where a user is granted a higher privilege level to accomplish a task or take on a role, for example when a user changes their password.
shared.image.missing_image
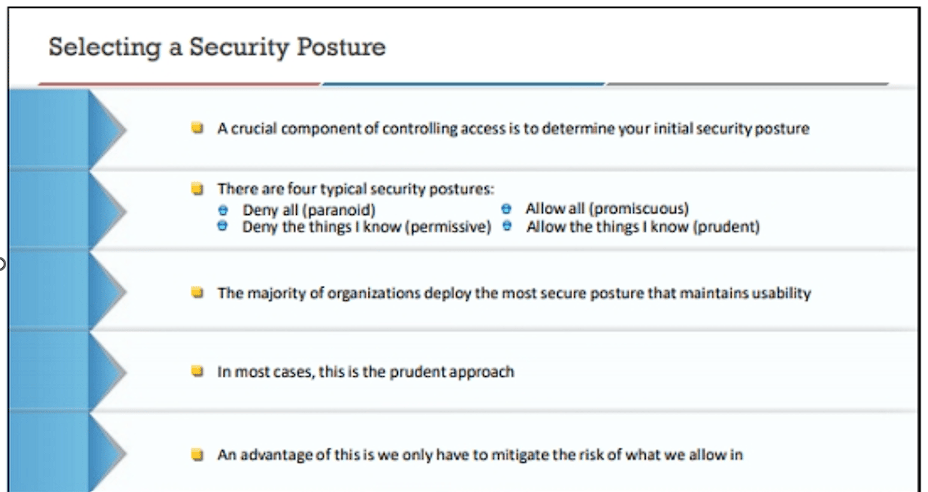
The reality is when you break it down, all of our systems and networks rely on a security policy and the choice of which posture to select is very easy to make.
While we might want to use the Paranoid approach, we cannot because the services have to be allowed and with the Paranoid approach nothing is allowed, so we cannot select it.
Next, we have the promiscuous mode which is basically allow everything and accept un-manageable risk, but if you do this then there is no way to secure it, so this is not the approach that we want to take.
Selecting a security Posture
Since we cannot use either of the first two, our decision comes down to one of the remaining two, but again there is only one that makes sense, but we want to evaluate this and make sure we are correct in this assumption. The Permissive approach results in blocking what we know is bad and then allowing everything else, in effect a setting of default permit, the problem with this approach is we never really know everything bad, so by doing this we allow the unknown. This is not something we ever want to do; therefore, the only choice is the Prudent security posture, and this is why we allow what we need and deny everything else by default deny! An advantage of this is we only have to track the vulnerabilities of what we have allowed by policy and as a result of this the risk from that. By doing this we can make it much easier to manage the risk and the security of our networks.
Defining Risk
Technology continues to develop in amazing, and sometimes alarming ways. Today, our personal relationships, work schedules, and business decisions not only make use of technological tools, they often rely on them, and this opens the door to intrepid hackers. Easy access to reams of sensitive information means more and more organizations are exposed to a range of cyber risks from data theft and ransomware to corporate espionage – and they may not even know it.
We must determine the risk from the services that are allowed by policy and that is where the risk equation comes in. There are many different references for risk. For our purposes, we will use the definition we have here. Once we have assessed this existing risk, we can determine what protections need to be put in place to mitigate or if possible, eliminate our risk.
Key Takeaways
This article explored essential security concepts for OT systems. We examined a data flow model where attackers exploit vulnerabilities like unauthorized access and data tampering. This model emphasizes Authentication for robust security, going beyond the traditional CIA triad.
A "prudent" security posture is crucial. Unlike overly restrictive or permissive stances, it allows authorized actions and denies everything else, minimizing risk and simplifying security management.
Finally, understanding the risks associated with allowed services empowers organizations to mitigate or eliminate them. This proactive approach ensures the overall security of your OT systems. By grasping these core security principles and implementing a prudent security posture with effective risk management, you can significantly improve the security of your critical industrial control systems.