Smart Meter Cybersecurity: Protecting Our Modern Grid Part -1
In this series of newsletters, we will cover the main parts of a smart meter, the cyber risks linked to it, and the challenges involved.
As our power grids become increasingly digital, understanding the components, risks, and challenges of securing smart metering infrastructure is crucial for industry professionals and policymakers alike.
Understanding Smart Meter Components
Let's break down the key elements of a smart metering system:

Smart Meter Infrastructure
Smart Meters
Advanced digital devices are increasingly replacing traditional analog meters, offering a more modern and efficient way to measure electricity consumption. These state-of-the-art digital meters provide real-time data on electricity usage, allowing for more accurate monitoring and
Often include:
Microprocessor for data processing
Memory for storing consumption data
Communication module (e.g., cellular, RF, PLC)
Display for showing consumption information
Disconnect switch for remote connect/disconnect

Communication Network
Communication Networks
Facilitate seamless two-way communication channels between smart meters and utility companies to enhance data exchange and operational efficiency.
Types include:
Wireless networks (e.g., cellular, RF mesh)
Power Line Communication (PLC)
Fiber optic networks
Often use a hierarchical structure with local concentrators/collectors

IN Smart meter HES and MDM systems
Head-End Systems (HES)
Centralized management systems designed for the efficient collection and analysis of meter data across various utilities and services.
Key functions:
Data collection and storage
Remote meter management
Firmware updates
Network management
Meter Data Management Systems (MDMS)
Comprehensive software platforms designed for the efficient processing and in-depth analysis of meter data, which include functionalities for data collection, storage, visualization, and
Capabilities include:
Data validation and estimation
Billing determinant calculations
Reporting and analytics
Integration with other utility systems (e.g., CIS, OMS)

Consumer interface
Consumer Interfaces
Web portals or mobile applications designed for enhancing customer engagement and interaction.
Features often include:
Real-time consumption monitoring
Historical usage analysis
Bill estimation tools
Energy-saving tips
Security Systems
Dedicated and comprehensive cybersecurity measures are in place to protect the Advanced Metering Infrastructure (AMI) ecosystem, ensuring the integrity, confidentiality, and availability of data
May include:
Intrusion detection/prevention systems
Security information and event management (SIEM) tools
Public key infrastructure (PKI) for device authentication
Firewalls and network segmentation
Let discuss in detail few more security Aspects in Unified way.
Unified Security Measures:
Simultaneous applications of different safety measures, such as network monitoring solutions, encryption, authentication, and supervisory systems like SCADA or Data Analytics, can and will play a key role in securing smart grid AMIs. Alongside, there exists an imminent need to acknowledge indicators of suspicious behavior. It additionally requires dedicated incident investigation and scoping to differentiate genuine causes of concern from false positives. The investigation findings are used to set up advanced firewalls, prevent unauthorized access, and secure smart grid assets.
A More Comprehensive and Effective Regulatory Framework:
End-users’ lack of precaution about these issues can easily compromise the AMI data, even with encryption. Adversaries can easily subject most users’ shared keys to inference and access. Regulatory frameworks are necessary to prevent unwanted access to users’ data. For instance, the General Data Protection Regulation (GDPR) has mandated data collecting online services in Europe. It informs users about the data collection methodologies and gets their consent. They also need to ensure that data storage is in a secure location. Moreover, they share it with third parties within defined time frames.
Data Loss Prevention Techniques:
Data encryption stands as a cornerstone of Data Loss Protection (DLP) in smart grids. Equally important are measures such as Role-based Access Control (RBAC), robust password policies, Multi-Factor Authentication (MFA), intrusion prevention systems (IPS), intrusion detection systems (IDS), data backup, and disaster recovery mechanisms. These strategies collectively fortify the grid against data breaches and uphold data integrity. The key to success lies in the comprehensive and tailored implementation of these techniques for smart grid applications.
Blockchain:
Using blockchain technology and smart contracts for AMI security makes each transaction more secure. AMIs store data about energy use, payments, and bills. We can also set conditions to avoid single points of failure in the smart grid system, whether it's for security or managing energy production, distribution, and monitoring. Blockchain is a very effective way to protect the privacy of all users and AMI data. Recent studies have suggested a dependable energy scheduling model using smart contracts and blockchain. This can help solve privacy issues in centralized systems that manage personal and financial information.
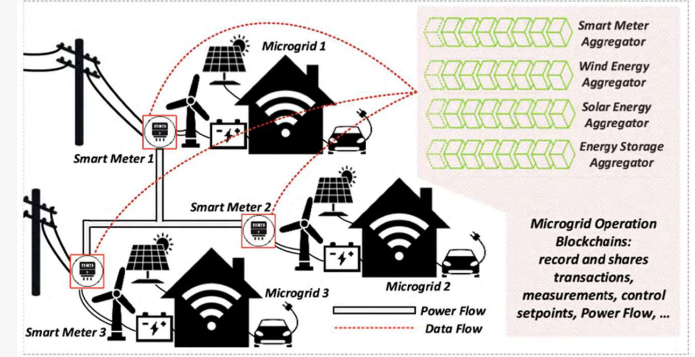
Blockchain For Advanced Metering Infrastructure Data Security
AI and ML:
Artificial intelligence and machine learning techniques can analyze high volumes of data, patterns, and anomalies in much less time. AMI also enhances security, speeds up threat response, offers better intrusion detection, and automates incident response.
Final Word
The lifeblood of intelligent energy networks is irreplaceable, and any breach can ripple through every connected meter and the entire web of connections. Upholding established standards and protocols is vital for safeguarding the integrity and privacy of these sophisticated systems and their users. As threats and technologies advance, so too must our defenses. Deploying cutting-edge data security measures is paramount for achieving peak performance. These efforts aim to dramatically bolster the overall security and efficiency of smart grid infrastructures. Grasping these elements is essential for understanding the cybersecurity hurdles faced by smart metering systems. In our next chapter, we'll delve into the risks and primary challenges in fortifying this intricate ecosystem.
Looking Ahead:
We're excited to announce that in our next installment, "AI-Enhanced Security for Advanced Metering: Navigating the New Frontier - Part 2: Cybersecurity Risks and Challenges," we'll be exploring the cutting-edge intersection of artificial intelligence and AMI security. We'll delve into the unique cybersecurity risks facing advanced metering systems and examine the challenges of implementing AI-driven security solutions.
What to expect in Part 2:
A comprehensive overview of current and emerging cybersecurity threats to AMI
An analysis of the specific challenges in securing distributed metering networks
Insights into how AI is being leveraged to detect and respond to security incidents
Discussion of the ethical considerations in using AI for AMI security
We look forward to continuing this journey with you as we navigate the exciting and critical field of AMI cybersecurity in the age of AI. Stay tuned for Part 2, coming in our next issue!