Special Message: Dear Reader
Before we begin, do me a favour and make sure you hit the “Subscribe” button to let me know that you care and keep me motivated to publish more. Thanks!
Learn how to make AI work for you
AI won’t take your job, but a person using AI might. That’s why 1,000,000+ professionals read The Rundown AI – the free newsletter that keeps you updated on the latest AI news and teaches you how to use it in just 5 minutes a day.
In the ever-evolving realm of Operational Technology (OT) cybersecurity, achieving robust segmentation is crucial for ensuring the security and integrity of critical infrastructures. The ISA/IEC 62443 standard provides a comprehensive framework for establishing secure architectures through zones and conduits. Drawing inspiration from The Art of War, where understanding the battlefield is key to victory, proper segmentation serves as your "battle plan" in cybersecurity. Just as careful preparation prevents defeat, a well-designed segmentation strategy offers organizations control over their security "terrain," allowing them to defend against potential threats and strengthen resilience.
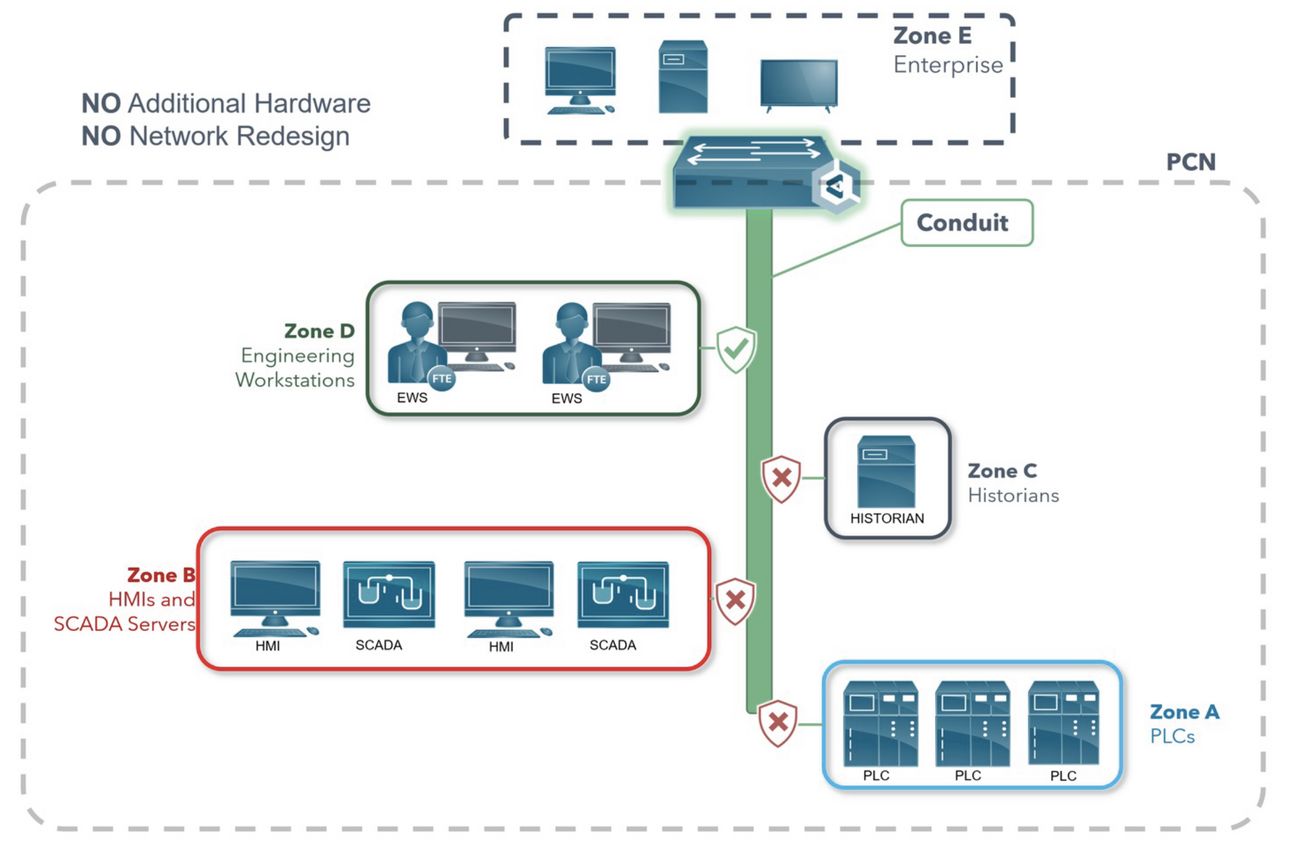
Understanding the Role of Segmentation in OT Cybersecurity
Segmentation within the context of ISA/IEC 62443 is not just a technical necessity; it is a strategic approach that allows you to partition your systems into manageable and secure segments, enhancing the overall cybersecurity posture of your OT environment. At its core, segmentation involves dividing a system under consideration (SuC) into zones (groups of assets with similar security requirements) and conduits (controlled communication pathways between zones). This structured approach enables efficient management of assets, enhances security, and simplifies compliance with regulations.
The Role of Zones and Conduits

Zones and conduits in ISA/IEC 62443 empower organizations to manage their cybersecurity landscape with precision and control. Each zone represents a distinct area within the system where assets share similar security needs, while conduits regulate the flow of information between these zones, ensuring secure communication and mitigating the risk of unauthorized access.
Segmentation through zones and conduits provides numerous advantages:
Control Over Critical Systems: Segmentation allows organizations to isolate critical systems, ensuring they remain unaffected by issues arising in other parts of the network.
Enhanced Security: By separating systems based on criticality, organizations can apply tailored security measures that meet the unique requirements of each zone.
Scalability and Resilience: Structured segmentation simplifies system management, improving both resilience against attacks and scalability in growing operational environments.
Aspect | Details |
|---|---|
Segmentation Definition | Segmentation divides systems into zones (assets with similar security needs) and conduits (controlled communication pathways between zones). |
Purpose of Segmentation | Enhances security, manages assets efficiently, and simplifies regulatory compliance. |
The Role of Zones and Conduits | Advantages |
|---|---|
Control Over Critical Systems | Isolates critical systems to ensure they remain unaffected by issues in other parts of the network. |
Enhanced Security | Enables tailored security measures based on the criticality of each zone, improving protection. |
Scalability and Resilience | Simplifies system management, improving resilience against attacks and scalability in growing environments. |
Key Drivers for Segmentation in ISA/IEC 62443

The ISA/IEC 62443 standard emphasizes segmentation due to several critical factors that directly impact the security and efficiency of OT environments. These include:
Asset Grouping: Zones enable grouping of assets with similar cybersecurity requirements, ensuring that they are managed consistently.
Separation by Criticality: Systems with varying levels of criticality can be physically or logically separated to enhance security. This reduces the risk of cross-contamination between high- and low-criticality systems.
Risk Management: Segmentation simplifies risk management by enabling targeted approaches for each zone based on the specific needs and vulnerabilities of its assets.
Controlled Communication: Conduits facilitate controlled, authorized communication between zones, supporting compliance with security standards and ensuring that only permitted traffic flows between systems.
Compliance and System Resilience: The segmentation model helps organizations comply with regulatory standards while enhancing system resilience through defined, monitored interactions between network segments.
The Segmentation Process According to IEC 62443
The partitioning of the system under consideration (SuC) into zones and conduits as defined by IEC 62443 follows a structured and methodical approach, which includes:
Establishment of Zones and Conduits: Identifying and defining the key zones based on the nature of the assets and their associated cybersecurity requirements.
Separation of Business and Control System Zones: Isolating business systems from control systems to reduce the risk of cyber threats spreading from administrative to operational systems.
Separation of Safety-Critical Zones: Ensuring that safety-critical systems are isolated to prevent unauthorized access and tampering, which could result in operational hazards.
Separation of Temporarily Connected Devices: Ensuring that any devices that are connected on a temporary basis are segregated to reduce the risk of introducing vulnerabilities.
Separation of Wireless Communications: Isolating wireless systems from the primary control networks to minimize exposure to external threats.
Separation of Untrusted Networks: Isolating devices connected via untrusted networks to mitigate risks of intrusion from insecure network connections.
Zone and Conduit Drawings: Developing detailed diagrams to document the physical and logical separation of zones and conduits.
Documentation of Characteristics: Recording the security requirements, access controls, and communication policies for each zone and conduit for compliance and auditing purposes.
Criteria for Segmentation in ISA/IEC 62443
When segmenting the SuC into zones and conduits, certain critical criteria must be carefully considered to ensure a robust and resilient architecture:
The partitioning of the SuC into zones and conduits as defined by IEC 62443:
Partitioning Step
Description
Establishment of Zones and Conduits
Identifying and defining zones (grouping assets) and conduits (controlling communication between zones) within the SuC.
Separation of Business and Control Systems
Isolating business systems from control systems to prevent cyber threats from spreading across different functional areas.
Separation of Safety-Critical Zones
Isolating safety-critical systems to ensure they are not compromised by unauthorized access or interference from less critical zones.
Separation of Temporarily Connected Devices
Ensuring devices that are only occasionally connected are kept isolated to prevent potential security vulnerabilities.
Separation of Wireless Communications
Isolating wireless systems from primary control networks to reduce risks from external threats and unsecured communication channels.
Separation of Devices on Untrusted Networks
Ensuring that devices connected via untrusted networks are properly isolated to prevent exposure to cyber risks.
Zone and Conduit Drawings
Creating detailed diagrams to visually represent the separation of zones and conduits within the system.
Documentation of Zone and Conduit Characteristics
Recording the characteristics, security requirements, and access controls of each zone and conduit for auditing and compliance.
This table provides a clear and structured breakdown of the key steps involved in the partitioning of systems using zones and conduits as per IEC 62443.
The criteria that should be considered when partitioning the SuC (System under Consideration) into zones and conduits:
Criteria
Description
Risk to Assets (Integrity, Availability, Confidentiality)
Assessing the level of risk to the assets in terms of maintaining data integrity, ensuring system availability, and protecting the confidentiality of information.
Type of Interfaces/Connections
Considering the type of connections between assets, such as wireless, wired, or external, to determine how best to isolate or control communication.
Physical or Logical Location
Taking into account the geographical or network-based placement of assets to decide on appropriate zoning and access control strategies.
Access Requirements
Defining who needs access to each zone and under what conditions, ensuring that only authorized personnel or systems can interact with the assets.
Operational Function
Grouping assets based on their operational roles (e.g., control systems, business functions) to create zones that align with functional requirements.
Organizational Responsibilities
Aligning zones with the organization’s structure, assigning responsibilities for managing, maintaining, and securing each asset or group of assets.
Safety Aspects
Ensuring that safety-critical systems are isolated to protect human life and essential operational functions from cybersecurity risks.
Technology Lifecycle
Considering the product lifecycle of assets, including obsolescence and future upgrades, to ensure that zones remain secure and adaptable over time.
This table outlines the important factors to keep in mind when structuring zones and conduits in an OT environment to enhance security and operational effectiveness.
Here is a table that outlines the key factors underscoring the need for segmentation in ISA/IEC 62443:
Key Factor
Description
Grouping of Assets
Zones allow assets with similar cybersecurity requirements to be grouped together, ensuring consistent security management across each zone.
Logical/Physical Separation of Systems
Segmentation enables the separation of systems based on their criticality, enhancing security by isolating high-criticality systems from less critical ones.
Simplified Risk Management
Zoning helps address the specific security needs and risks of each zone, streamlining the process of risk assessment and management.
Controlled Communication Between Zones
Conduits facilitate secure, authorized communication between zones, ensuring that data flows are controlled and restricted, supporting compliance with security standards.
Enhanced System Resilience and Scalability
Proper zoning and segmentation contribute to a more resilient system architecture that can better withstand cyber threats while also supporting system scalability.
This table provides a clear summary of why segmentation is vital for effective OT cybersecurity management, particularly when applying ISA/IEC 62443 standards.
Segmentation Task | Description |
|---|---|
Zone and Conduit Model Implementation IEC 62443-3-2 | Dividing the industrial control system into logical zones based on security requirements, criticality, and business needs. Each zone contains devices with similar security requirements and trust levels. |
Security Level Assessment IEC 62443-3-2, IEC 62443-3-3 | Determining the target Security Level (SL-T) for each zone based on risk assessment and potential impact of security breaches. Levels range from SL 1 to SL 4. |
Boundary Protection IEC 62443-3-3 | Implementing security controls at zone boundaries, including firewalls, DMZs, and other network security measures to control and monitor traffic between zones. |
Network Segmentation IEC 62443-3-3, IEC 62443-4-2 | Physical or logical separation of networks to isolate critical control system components from less secure networks, including IT networks and the internet. |
Access Control Management IEC 62443-3-3 | Establishing and maintaining access controls between zones, including user authentication, authorization mechanisms, and privilege management. |
Communication Control IEC 62443-3-3, IEC 62443-4-1 | Defining and implementing secure communication paths (conduits) between zones, including protocol filtering and data flow control. |
Defense in Depth IEC 62443-3-3 | Implementing multiple layers of security controls across zone boundaries to provide redundant protection against security threats. |
Monitoring and Logging IEC 62443-3-3 | Setting up security monitoring and logging mechanisms at zone boundaries to detect and track unauthorized access attempts and security events. |
Documentation IEC 62443-2-1, IEC 62443-3-2 | Maintaining detailed documentation of zone definitions, security requirements, and implemented controls for audit and compliance purposes. |
Periodic Review IEC 62443-2-1 | Regular assessment and updates of zone segmentation to ensure alignment with changing security requirements and emerging threats. |
Conclusion: Segmentation as a Strategic Approach
Segmentation is not merely a technical measure; it is a strategic approach to gaining control over your OT environment. By leveraging the power of zones and conduits as defined by ISA/IEC 62443, organizations can achieve enhanced security, compliance, and operational efficiency. As cybersecurity threats become increasingly sophisticated, the implementation of a robust segmentation strategy will provide the "battle plan" needed to defend critical infrastructures and ensure long-term resilience.
By taking a methodical approach to segmentation, organizations can reduce risk, streamline security management, and ensure that their systems are prepared to face the challenges of the modern cybersecurity landscape.
Thanks for reading - until next edition!
Editor Article Recommendation of the Week
Editor Recommendation to read the related article