Want SOC 2 compliance without the Security Theater?
Oneleet is the all-in-one platform for SOC 2 Compliance & Attestation.
Get the automation software, penetration test, 3rd party audit, and vCISO services in one place!
Focus on what matters to build real-world security & pass security reviews!

Updated Cybersecurity Guidelines in Next CEA: Important Information for Tech Integrators, Auditors, and Regulators
In South Asia, things are changing. Rules are becoming stricter every day. In India, the power sector is preparing for these changes. The Central Electricity Authority (CEA) recently shared a draft that demonstrates their careful planning and strategy.
Amidst the anticipated revisions to the Central Electricity Authority's (Cyber Security in Power Sector) Regulations in 2024, the current draft, now open for public commentary, underscores pivotal aspects that resonate deeply with a TIC firm adept in IEC 62443 certification and assessment. This draft not only lays the regulatory groundwork for such specialized services but also delineates the precise obligations that power sector entities must fulfill—areas where your expertise can provide invaluable assistance.
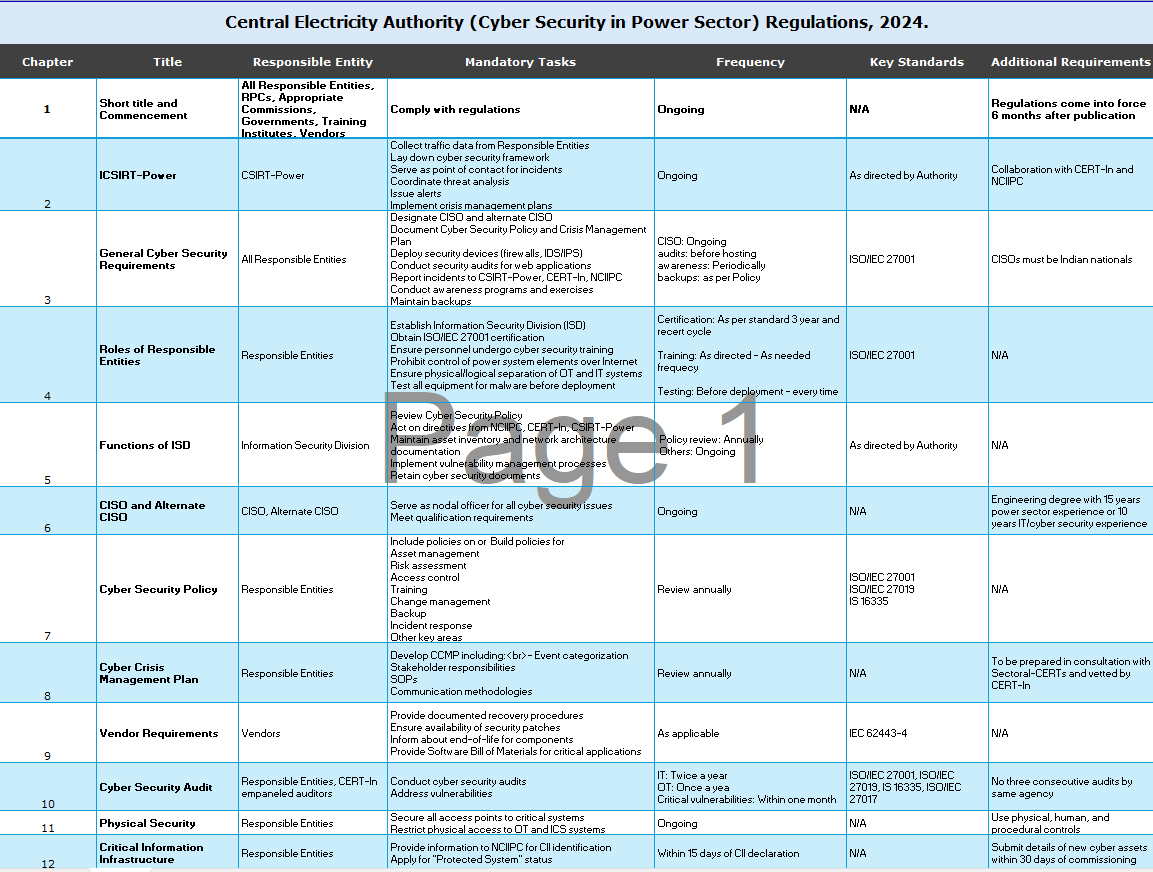
We have summarised the key changes in regulatory requirements for the power industry in India and the South Asia market segment for you..
Central Electricity Authority (Cyber Security in Power Sector) Regulations, 2024.

you can download the original source .XLs file showed above with this link
Let us highlight a few key facts from the draft with reference to what they have quoted. The Central Electricity Authority (CEA) discusses multiple standards that need to be adhered to, specifying who is responsible for ensuring compliance with these standards. Additionally, the CEA defines the frequency at which these standards should be followed. This comprehensive approach aims to ensure that all relevant parties are aware of their responsibilities.
This discussion focuses on essential insights for TIC, asset owners, and power industry stakeholders.
Certificaiton requirments
Auditing and assesment
Scope of Assesment
Stakeholder to engage
Alignment to other standards
Future opportunity
Competency requirements
1. Certification Requirements
IEC 62443 Compliance for Vendors:
Reference: Chapter XI, Article 23 refer: "The vendor shall ensure that all OT equipment/systems supplied by them are accompanied by a certificate obtained by the vendor from a certification body for conformance to IEC 62443-4 standards."
ISO/IEC 27001 Certification for Responsible Entities:
Reference: Chapter IV, Article 8(2) Quote: "Responsible Entities shall acquire ISO/IEC 27001 certificate by certification bodies, preferably accredited by the Indian Accreditation Body..."
2. Audit and Assessment Opportunities
Regular OT System Audits:
Reference: Chapter III, Article 7(11)(B)
Quote: "once a year for the OT system, as applicable."
Comprehensive Cyber Risk Assessments:
Reference: Chapter VII, Article 16(3)
Quote: "Cyber risk assessment shall be conducted annually and shall consider but not limited to, all cyber assets identified/notified as Critical Information Infrastructure/Protected Systems, critical and high-risk cyber assets..."
Vulnerability Assessments:
Reference: Chapter VII, Article 16(5)
Quote: "Vulnerability Management Process for periodic identification and closure of vulnerabilities,"
3. Scope of Assessments
OT Security Focus:
Reference: Chapter IV, Article 8(8), 8(9)
Quote: "ensure physical isolation of critical OT system from Internet." and "ensure physical separation between critical OT system and enterprise IT system."
Supply Chain Security:
Reference: Chapter VII, Article 16(19)
Quote: "plan for Cyber Supply Chain Risk Management that includes provision of Cyber Security requirements in outsourcing and Non-Disclosure Agreement in the Service Level Agreement."
Patch and Change Management:
Reference: Chapter VII, Article 16(9)
Quote: "defined and documented Change Management process to ensure that all changes in software and/or update shall be version controlled with roll-back provision."
4. Stakeholders to Engage
Responsible Entities:
Reference: Chapter I, Article 2(a)(25)
Quote: "'Responsible Entities' shall mean power sector entities deploying Operational Technologies with or without IT systems, including Generating companies..."
Vendors:
Reference: Chapter I, Article 2(a)(29)
Quote: "'Vendors' includes Original Equipment Manufacturer, Original Equipment Suppliers, System Integrator, Associated Hardware/ Software Component Suppliers, and Service Providers."
Information Security Divisions (ISDs):
Reference: Chapter IV, Article 8(1)
Quote: "Responsible Entities shall establish an Information Security Division (ISD) dedicated to ensuring Cyber Security, headed by the CISO and remain operational round the clock."
Chief Information Security Officers (CISOs):
Reference: Chapter VI, Article 12
Quote: "CISO & Alternate CISO shall possess a degree in Engineering with at least fifteen years of experience in power sector domain or 10 years of experience in IT/Cyber Security."
5. Alignment with Other Standards
Integration with Multiple Standards:
Reference: Chapter X, Article 25
Quote: "These Cyber Security audits shall be carried out as per ISO/IEC 27001 along with sector specific standard ISO/IEC 27019, IS 16335, ISO/IEC 27017 and any other Cyber Security audit directions issued by the Authority."
6. Future Opportunities
Basic Technical Criteria (BTC) Certification:
Reference: Chapter IV, Article 8(2)
Quote: "...or acquire Basic Technical Criteria certificate as and when issued by the Authority through a separate order."
Trusted Vendor System:
Reference: Chapter II, Article 4(12)
Quote: "Implementation of Scheme of Trusted Vendor System for Power Sector as and when notified."
7. Competency Requirements
Auditor Qualifications:
Reference: Chapter X, Article 25
Quote: "The Cyber Security audit shall be conducted through a CERT-In empanelled Cyber Security Auditor or cyber security auditor as per NCIIPC scheme as and when the same comes into existence."
OT-Specific Expertise:
Reference: Chapter IV, Article 8(3)
Quote: "ensure that all personnel engaged in the operation and maintenance of IT & OT systems, including personnel from Contractors and Vendors, have mandatorily undergone designated Cyber Security courses from training institutes as directed by the Authority through a separate order."
The Central Electricity Authority (CEA) has issued draft regulations aimed at bolstering cyber security within the power sector. These regulations, titled "CEA (Cyber Security Regulations for the power sector) Regulations, 2024," outline comprehensive measures for enhancing the resilience of the power sector against cyber threats.
Want SOC 2 compliance without the Security Theater?
Oneleet is the all-in-one platform for SOC 2 Compliance & Attestation.
Get the automation software, penetration test, 3rd party audit, and vCISO services in one place!
Focus on what matters to build real-world security & pass security reviews!
Key Aspects of the Draft Regulations:
Scope: The regulations apply to all responsible entities, regional power committees, appropriate commissions, governments, and related organizations in the power sector. This includes training institutes and vendors involved in the sector.
CSIRT
Response to cyber incident
IS divission
Vendor requirments
CSIRT-Power Responsibilities:
Establishing a cyber security framework for the power sector.
Responding effectively to cyber incidents.
Coordinating with other national cyber security bodies such as CERT-In and NCIIPC.
Information Security Division:
Entities must establish a dedicated Information Security Division (ISD) responsible for cyber security.
The ISD will handle critical infrastructure protection, policy reviews, and regular security assessments.
Vendor Requirements:
Vendors must provide documented and tested procedures, along with a recovery plan, for restoring systems in the event of a cyber crisis.
Vendors are also required to ensure that security patches and updates are available for all system components they supply throughout the contractually agreed operating period.
These regulations aim to strengthen the cyber security posture of the power sector by ensuring that all stakeholders, including vendors, are actively involved in safeguarding critical infrastructure. The draft is currently open for feedback and may undergo revisions before being finalized.
Want SOC 2 compliance without the Security Theater?
Oneleet is the all-in-one platform for SOC 2 Compliance & Attestation.
Get the automation software, penetration test, 3rd party audit, and vCISO services in one place!
Focus on what matters to build real-world security & pass security reviews!
We suggest you update your email preferences to avoid spam. You can do this by going to the end of this newsletter and clicking on "Preferences" to choose how often you want to receive emails and what topics interest you.